- Pkcs11-tool Generate Key Pair Key
- Pkcs11-tool Generate Key Pair Keyboard
- Pkcs11-tool Generate Key Pair App
An Online RSA Public and Private Key Generator. I was recently in a meeting where a person needed to generate a private and public key for RSA encryption, but they were using a PC (Windows). Generate a new key pair (public and private pair.) -key-type specification Specify the type and length of the key to create, for example rsa:1024 or EC:prime256v1.usage-sign Specify 'sign' key usage flag (sets SIGN in privkey, sets VERIFY in pubkey).
This will generate a public and private key pair. The keyspec consist of the key type, rsa or dsa (depends on what your card supports), and optinally a slash followed by the keysize in bits. 'rsa/1024' specifies a 1024-bit RSA key pair. Note: dsa is not fully supported. 2.1.5 X9.31 RSA key pair generation. The X9.31 RSA key pair generation mechanism, denoted CKMRSAX931KEYPAIRGEN, is a key pair generation mechanism based on the RSA public-key cryptosystem, as defined in X9.31. It does not have a parameter.
A public-key cryptography, also known as asymmetric cryptography, is a class of cryptographic algorithms which requires two separate keys, one of which is secret (or private) and one of which is public.1 Together they are known as a key-pair. In SSH, the public key cryptography is used in both directions (client to server and server to client. C: Program Files (x86) OpenSC Project OpenSC toolspkcs15-init.exe -create-pkcs15 -profile pkcs15+onepin -use-default-transport-key -pin 0000 -puk 111111 -label 'ePass2003' Using reader with a card: FS USB Token 0 2014-07-29 22:35:08.208 cannot lock memory, sensitive data may be paged to disk 2014-07-29 22:35:08.442 cannot lock memory. I've tried to export the key using pkcs11-tool, but it did not work for me. I assume that this template is used to generate a key pair for a Certificate Authority.
pkcs11-tool (1)
Leading comments
NAME
pkcs11-tool - utility for managing and using PKCS #11 security tokensSYNOPSIS
- pkcs11-tool [OPTIONS]
DESCRIPTION
Thepkcs11-toolutility is used to manage the data objects on smart cards and similar PKCS #11 security tokens. Users can list and read PINs, keys and certificates stored on the token. User PIN authentication is performed for those operations that require it.OPTIONS
--attr-frompath
- Extract information frompath(DER-encoded certificate file) and create the corresponding attributes when writing an object to the token. Example: the certificate subject name is used to create the CKA_SUBJECT attribute.
--change-pin, -c
- Change the user PIN on the token
--unlock-pin
- Unlock User PIN (without--loginunlock in logged in session; otherwise--login-typehas to be 'context-specific').
--hash, -h
- Hash some data.
--idid, -did
- Specify the id of the object to operate on.
--init-pin
- Initializes the user PIN. This option differs from--change-pinin that it sets the user PIN for the first time. Once set, the user PIN can be changed using--change-pin.
--init-token
- Initialize a token: set the token label as well as a Security Officer PIN (the label must be specified using--label).
--input-filepath, -ipath
- Specify the path to a file for input.
--keypairgen, -k
- Generate a new key pair (public and private pair.)
--key-type <replacement>specification</replacement>
- Specify the type and length of the key to create, for example rsa:1024 or EC:prime256v1.
--usage-sign
- Specify 'sign' key usage flag (sets SIGN in privkey, sets VERIFY in pubkey).
--usage-decrypt
- Specify 'decrypt' key usage flag (RSA only, set DECRYPT privkey, ENCRYPT in pubkey).
--usage-derive
- Specify 'derive' key usage flag (EC only).
--labelname, -aname
- Specify the name of the object to operate on (or the token label when--init-tokenis used).
--list-mechanisms, -M
- Display a list of mechanisms supported by the token.
--list-objects, -O
- Display a list of objects.
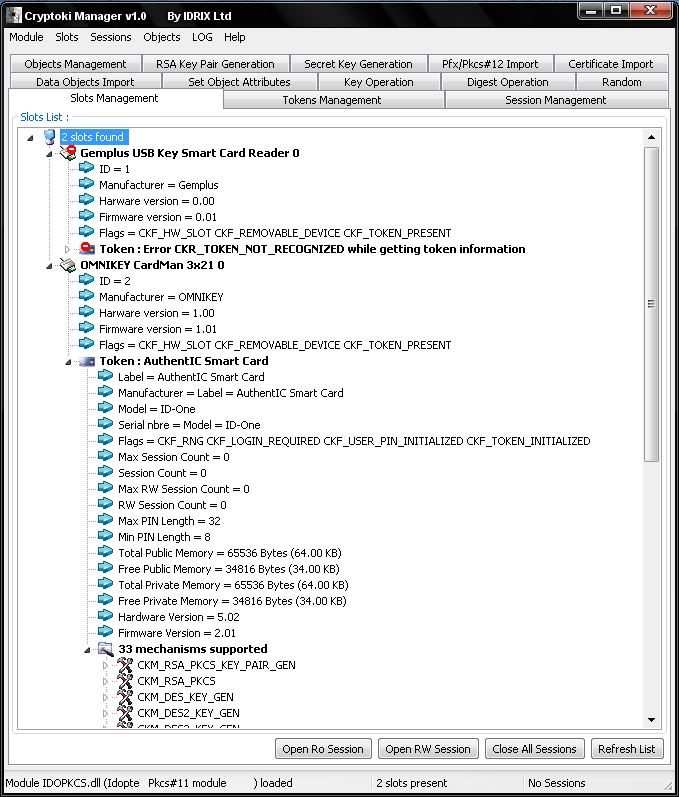
--list-slots, -L
- Display a list of available slots on the token.
--list-token-slots, -T

- List slots with tokens.
--login, -l
- Authenticate to the token before performing other operations. This option is not needed if a PIN is provided on the command line.
--login-type
- Specify login type ('so', 'user', 'context-specific'; default:'user').
--mechanismmechanism, -mmechanism
- Use the specifiedmechanismfor token operations. See-Mfor a list of mechanisms supported by your token.
--modulemod
- Specify a PKCS#11 module (or library) to load.
--moz-certpath, -zpath
- Test a Mozilla-like keypair generation and certificate request. Specify thepathto the certificate file.
--output-filepath, -opath
- Specify the path to a file for output.
--pinpin, -ppin
Use the givenpinfor token operations. If set to env:VARIABLE, the value of the environment variableVARIABLEis used. WARNING: Be careful using this option as other users may be able to read the command line from the system or if it is embedded in a script. If set to env:VARIABLE, the value of the environment variableVARIABLEis used.This option will also set the--loginoption.
--pukpuk
- Supply User PUK on the command line.
--new-pinpin
- Supply new User PIN on the command line.
--set-idid, -eid
- Set the CKA_ID of the object.
--show-info, -I
- Display general token information.
--sign, -s
- Sign some data.
--decrypt,
- Decrypt some data.
--derive,
- Derive a secret key using another key and some data.
--slotid
- Specify the id of the slot to use.
--slot-descriptiondescription
- Specify the description of the slot to use.
--slot-indexindex
- Specify the index of the slot to use.
--token-labellabel
- Specify the label of token. Will be used the first slot, that has the inserted token with this label.
--so-pinpin
- Use the givenpinas the Security Officer PIN for some token operations (token initialization, user PIN initialization, etc). If set to env:VARIABLE, the value of the environment variableVARIABLEis used. The same warning as--pinalso applies here.
--test, -t
- Perform some tests on the token. This option is most useful when used with either--loginor--pin.
--test-hotplug
- Test hotplug capabilities (C_GetSlotList + C_WaitForSlotEvent).
--private
- Set the CKA_PRIVATE attribute (object is only viewable after a login).
--test-ec
- Test EC (best used with the--loginor--pinoption).
--test-fork
- Test forking and calling C_Initialize() in the child.
--typetype, -ytype
Pkcs11-tool Generate Key Pair Key
- Specify the type of object to operate on. Examples arecert,privkeyandpubkey.
--verbose, -v
Causepkcs11-toolto be more verbose.NB! This does not affect OpenSC debugging level! To set OpenSC PKCS#11 module into debug mode, set theOPENSC_DEBUGenvironment variable to a non-zero number.
--read-object, -r
- Get object's CKA_VALUE attribute (use with--type).
--delete-object, -b
- Delete an object.
--application-labellabel
Pkcs11-tool Generate Key Pair Keyboard
- Specify the application label of the data object (use with--typedata).
--application-idid
- Specify the application ID of the data object (use with--typedata).
--issuerdata
- Specify the issuer in hexadecimal format (use with--typecert).
--subjectdata

- Specify the subject in hexadecimal format (use with--typecert/privkey/pubkey).
--signature-formatformat
- Format for ECDSA signature: 'rs' (default), 'sequence', 'openssl'.
--write-objectid, -wpath
- Write a key or certificate object to the token.pathpoints to the DER-encoded certificate or key file.
--generate-randomnum
Pkcs11-tool Generate Key Pair App
- Getnumbytes of random data.
Comments are closed.